
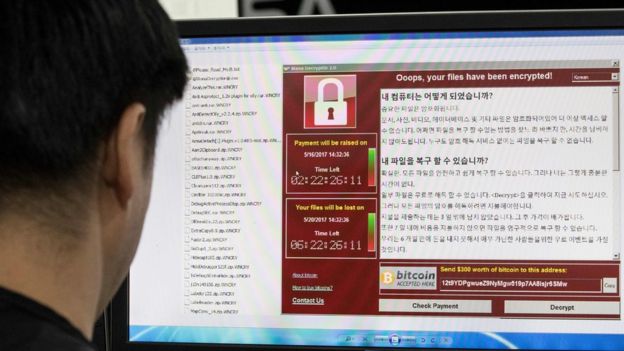
The WannaCry cyber-attack infected more than 200,000 computers in 150 countries, affecting government, healthcare and private company systems. But how easily could it have been avoided and how can firms protect themselves against future attacks?
On the face of it, the accepted narrative seems simple. Microsoft issued a patch, or update, for the vulnerability in its older Windows operating systems in March.
If all IT departments everywhere had implemented this patch immediately, the WannaCry ransomware worm wouldn’t have been able to run riot across the globe.
Although the hackers are thought to have extorted just £60,000 worth of bitcoins, the disruption was significant, with some patients having operations and appointments cancelled and some corporate data being lost for ever.
David Venable, vice-president of cyber-security at Masergy Communications, an IT services firm, is a former intelligence officer with the US National Security Agency.
He says: “There are a lot of practical challenges in deploying patch updates; from having unsupported operating systems [OSs] that don’t have patches available, through to the practicalities of rolling out sweeping changes across massive networks, potentially globally.
“But these aren’t new challenges – anyone running these networks should have had this solved long before now.
“This isn’t rocket science; it’s an oil change.”

And Rob Wainwright, director of Europol, believes that the recent failings in cyber defences were more to do with lack of leadership in large organisations than lack of IT investment.
“It’s frustrating frankly, because in the health sector there have been multiple ransomware attacks, in the United States, in Europe, for the last two years, long before WannaCry came along, and so the lessons should have been heeded by now,” he told the BBC.
According to the Verizon Data Breach Investigations Report 2017, ransomware accounts for 72% of malware incidents in the healthcare industry.
Overall, there has been a 50% rise in ransomware incidents reported in the last 12 months.
Complex systems
But how easy is it really to keep large, complex computer networks up-to-date and protected?
Nik Whitfield from security firm Panaseer says that for many large businesses, patching their systems isn’t a question of turning on “auto-updates” then sitting back and relaxing.
This is because some software applications specific to their business might rely on certain versions of operating systems (OS). Updating the OS could affect how those programs function.
It’s a point echoed by Adam Meyers, vice-president of cyber-security company CrowdStrike: “It is important to recognise that patch roll-outs are complex. High-profile patch fiascos have made IT departments wary of automatic patch installations.”
Some companies have suffered embarrassing shutdowns of their networks after patch roll-outs, for example.
Health service providers in the UK and abroad were particularly affected because they were often reliant on old versions of Windows, and also because important medical equipment supplied by third parties – MRI scanners, blood analysis systems and so on – can’t be easily upgraded or patched.
“Primarily this is because the patch may affect the equipment,” says Simon Edwards, European cyber security architect at Trend Micro, “but other times the vendor simply refuses to do it.”
Older companies that have acquired or merged with other firms over the years, will have built up a ragtag patchwork of legacy systems – sometimes hundreds of programs – all requiring maintenance.
“It always comes down to prioritisation,” says Mr Whitfield. “There’s always too much work to do, so they’re constantly looking at how best to spend that next security dollar.

“Patching a business is like trying to mend a moving vehicle that is made from a hundred different vehicles bolted together.”
This is why it can sometimes take months before known security vulnerabilities get patched.
And the brutal truth is that there are plenty of companies and organisations that simply don’t have enough IT staff or take cyber risk seriously enough, argues Mike DeCesare, chief executive of network security firm, ForeScout.
Top priorities
As well as keeping antivirus, firewall, application and OS software up-to-date, backing up key data regularly to offline hard drives should be a top priority, most cyber experts agree.
This is because data breaches and cyber-attacks are inevitable these days.
The bad news is that the average cost of a data breach globally stands at $4m (£3.1m), according to SailPoint, an identity management firm.
One common problem is that companies often don’t know what data they have, where it is, or what data is the most important, says Kirsten Bay, chief executive of network monitoring firm, Cyber Adapt.
“Concentrate on protecting the most critical data,” she says.
Cyber-security used to be about building an impregnable wall around your company. But now that hackers seem to be finding weak points in these perimeter defences with increasing ease – largely due to the proliferation of wireless devices accessing the network at home and in the office – focus has moved towards defending critical parts within the network.
“Once inside an organisation a hacker or malware will get around pretty quickly,” explains David Venable, “but if you take the ‘zero trust model’ approach and treat every network as hostile, a lot of this could have been prevented.”
In practice, this means constantly monitoring your network for unusual behaviour and only giving access to certain data and applications to those who absolutely need it.

Everyone else is treated as potentially hostile, even if they work for you.
“By identifying a suspicious process or behaviour and applying machine learning to let all other computers know about it, organisations can be on the front foot,” argues CrowdStrike’s Mr Meyers.
Trend Micro’s Simon Edwards warns companies against thinking there’s a simple one-size-fits-all solution to these cyber-security challenges.
“Companies should never rely on one technology or process to stop malware,” he says. “They need to use multiple methods which inter-operate with one another to detect and stop attacks.”
There is evidence that firms have been rushing out to buy security products in the aftermath of the WannaCry attack.
Erich Litch, chief revenue officer for software marketplace 2Checkout says: “In the US, the number of security software purchases is up 43% as organisations look to avoid the large-scale attacks seen in the UK.”

In the UK, sales have risen 25%, he says. “[But] panic buying security software is not the answer. Make cyber-security an active part of your strategy, not a reaction to a disaster.”
This takes board-level commitment to cyber-security, most experts agree.
Internet of things
The worry for businesses everywhere is that the cyber threat is only going to increase as the world becomes more connected and the internet of things (IoT) accelerates.
“In many cases IoT devices are either impossible to patch or at best very challenging to patch,” warns Paul Lipman, chief executive of BullGuard.
“We’re seeing billions of new devices entering businesses and homes, with little-to-no security built in, and challenging to update.
“This is a hacker’s dream and a recipe for a cyber-security disaster.”
At least the WannaCry attack has woken everyone up to the fact that the cyber-threat is real, growing and impossible to ignore any longer.
Source – BBC
THE ROTTEN FISH: CAN OF WORMS OPENED OF APC & TINUBU'S GOVERNMENT OVER NIGERIA'S ECONOMIC DOWNTURN
WATCH THE CRITICAL ANALYSIS AND KNOW THE RESPONSIBLE PARTIES TO BLAME FOR NIGERIA'S ECONOMIC CHALLENGES, WHILE CITIZENS ENDURE SEVERE HARDSHIPS.Watch this episode of ISSUES IN THE NEWS on 9News Nigeria featuring Peter Obi's Special Adviser, Dr Katch Ononuju, 9News Nigeria Publisher, Obinna Ejianya and Tinubu Support Group Leader, McHezekiah Eherechi
The economic crisis and hardship in Nigeria are parts of the discussion.
Watch, leave your comments, and share to create more awareness on this issue.
#9NewsNigeria #Nigeria #issuesInTheNews #politics #tinubu THE ROTTEN FISH: CAN OF WORMS OPENED ...
DON'T FORGET TO SUBSCRIBE AND LEAVE YOUR COMMENTS FOR SUBSEQUENT UPDATES
#9newsnigeria #economia #economy #nigeria #government @9newsng
www.9newsng.com
